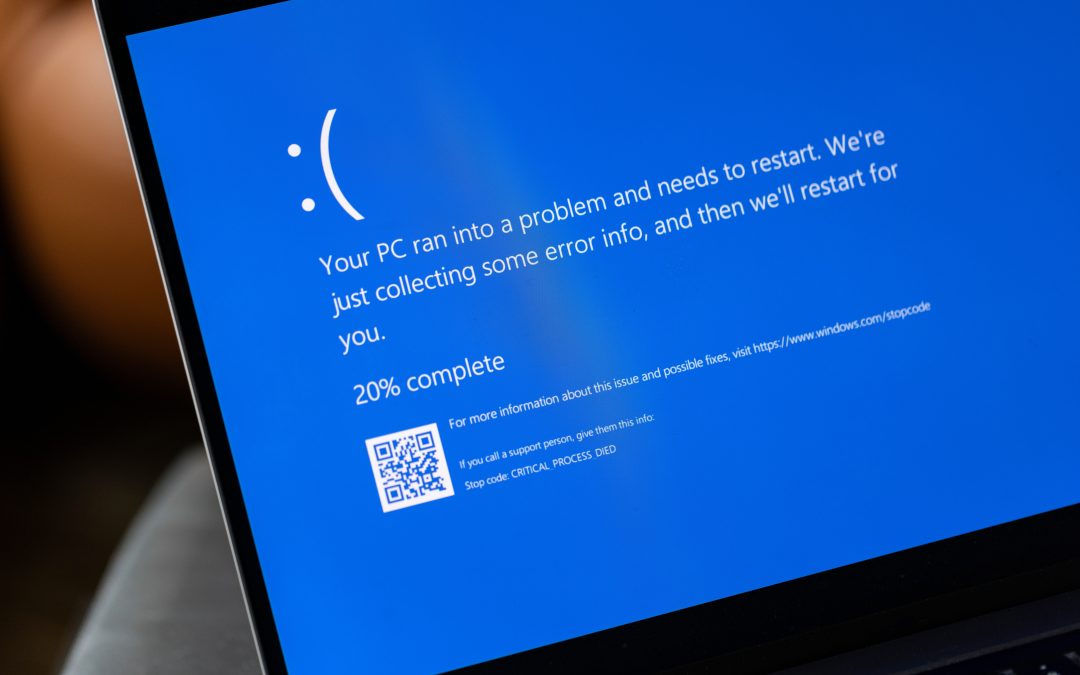
The recent CrowdStrike outage has brought to light significant cybersecurity risks that businesses must be vigilant about. On July 19, 2024, CrowdStrike’s Falcon Sensor vulnerability scanner update caused a critical flaw that led to widespread disruptions across millions of Microsoft Windows machines. This incident not only caused operational chaos but also opened doors for cybercriminals to exploit the situation.
The Immediate Impact
The flaw in the update led to blue screens of death, rendering computers unusable and causing major disruptions globally. Critical sectors, including aviation, banking, healthcare, and emergency services, were severely impacted. This chaos provided an opportunity for cybercriminals to impersonate tech support and infiltrate company systems.
The Rise of Impersonation Attacks
During such crises, the urgency to fix the problem can lead companies to let their guard down. Hackers are aware of this and often take advantage of the situation by posing as tech support representatives. Here are some ways they exploit these incidents:
- Phishing Emails: Cybercriminals send emails pretending to be from the affected company or from official tech support, urging recipients to click on malicious links or download harmful attachments.
- Phone Scams: They may call employees directly, claiming to be tech support and requesting remote access to their systems.
- Fake Websites: Hackers set up fake websites that mimic the official company’s support page, tricking users into entering sensitive information.
The Importance of Vigilance
To safeguard against these risks, companies need to implement robust security measures and maintain a high level of vigilance during such incidents. Here are some best practices to consider:
- Verify Tech Support: Always verify the identity of tech support representatives. Use known contact methods and double-check credentials before granting access.
- Educate Employees: Regularly train employees on how to recognize phishing attempts and other forms of social engineering attacks.
- Implement Multi-Factor Authentication (MFA): Ensure that all systems and applications are protected by MFA, making it harder for unauthorized individuals to gain access.
- Maintain Regular Backups: Keep regular backups of all critical data to ensure business continuity in case of system failures or breaches.
- Monitor for Suspicious Activity: Use advanced threat detection tools to continuously monitor for any unusual activity within your network.
CrowdStrike’s Response and Remediation
CrowdStrike has acknowledged the issue and provided a fix. Affected machines need to be manually fixed by booting into safe mode or Windows Recovery Mode and deleting the problematic configuration file. While this fix addresses the immediate problem, the incident underscores the need for thorough testing and vigilance.
Conclusion
The CrowdStrike outage is a stark reminder of the vulnerabilities that can arise even from trusted security providers. It highlights the importance of being prepared for unexpected incidents and the necessity of having a proactive cybersecurity strategy in place. By staying vigilant and implementing robust security measures, businesses can mitigate the risks associated with such disruptions and protect themselves from potential cyber threats.
Stay informed, stay secure, and ensure that your cybersecurity practices are always up to date to handle the evolving landscape of digital threats.
Contact us today to find out how to protect yourself and your business from threats like this and many more.